How Many Security Checks Your Website Needs
Author: jericaqueen
Published in: Web Development
How many security checks your website needs
The activities that can be carried out to carry out the security tests are diverse and are oriented in several areas, especially as regards to ensuring the operation and availability of the web services and published contents. In general, we refer to websites whose content is public and does not include strategic information or instructional security, for this reason, the correct configuration of servers and services must include verification of at least the following topics:
Without going into the detail of the elements to consider for this decision, the main recommendation is to make an objective evaluation based on the following aspects:
With these parameters, the best option must be defined, not only from the point of view of the interest of the technical areas but also through an overall impact assessment of the associated decision.
- DNS Handling
One aspect that must be taken care of is to use a suitable domain name and related to the identity and mission of the institution. However, thanks to the operation of the Domain Name Service (DNS), it is possible to assign more than one domain name to the same Website.
However, no matter how many aliases a site has, it is recommended that all domains be redirected so that the first screen, in any case, corresponds to the official website portal and that each domain is configured to respond Using the non-nomenclature "www".
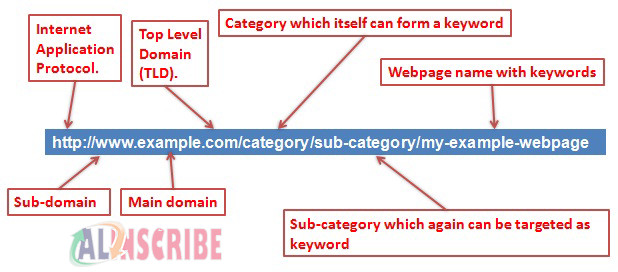
- Protection of the Internal Structure of the Website
One of the mechanisms that allows protecting the internal structure of the site (especially in cases of attempts of external attacks and / or attempts of violation of confidentiality), is to reduce the amount of information contained in the URLs that are shown in the viewer program. This is important with respect to directories and program names, but especially with regard to the delivery of session parameters, user data or other information transfer mechanism between pages and / or code sections. You can contact with a web development company regrading this issue as well.
It is recommended that the mechanisms of transfer of information between pages are at the level of server objects, associated with the session, without the interaction with the client side should be responsible for the transfer of data and / or information between server execution sessions.
- Privacy Policy
Maintaining user privacy should be a permanent goal of the site. This requires a formal and explicit Privacy Policy on the site and, in addition, there must be specific security mechanisms to protect the data of its users. Among these, physical and logical protections should be available.
In the case of having real multilayer architectures, it is recommended to protect client information on physical servers other than data storage, including ideally separated data query interfaces. In addition, incorporate data encryption mechanisms for sensitive information. It is recommended that information if it is stored for the purpose of retrieving it from the Web Site, be encrypted with keys managed by them (for example, their authentication key (identification) in front of the site).
- External Hosting vs. Own Site
- Evaluate the actual capacities available for the permanent operation of the site, from a technical point of view.
- Evaluate the necessary control and safety requirements.
- Evaluate the level of effective support that service technicians can perform on servers.
Article Comments
Articles Search
Sponsor
There are zero sub-categories in this parent category.
There are zero sub-categories in this parent category.
There are zero sub-categories in this parent category.
















